This writeup explores the CVE discovered by Ken Gannon and Ilyes Beghdadi at Pwn2Own 2023. The goal is to understand their exploitation techniques and the underlying issues, all within a controlled and ethical environment.Blog Video
Versions affected: 30.4.1.0 and Below
Name : GetApps Store Android Application (com.xiaomi.mipicks)
Author: Ken Gannon of NCC Group , Ilyes Beghdadi of Census Labs
Advisory URL / CVE Identifier: CVE-2024-4406
so as we start in android look at AndroidMainfast.xml there
com.xiaomi.market.ui.JoinActivity
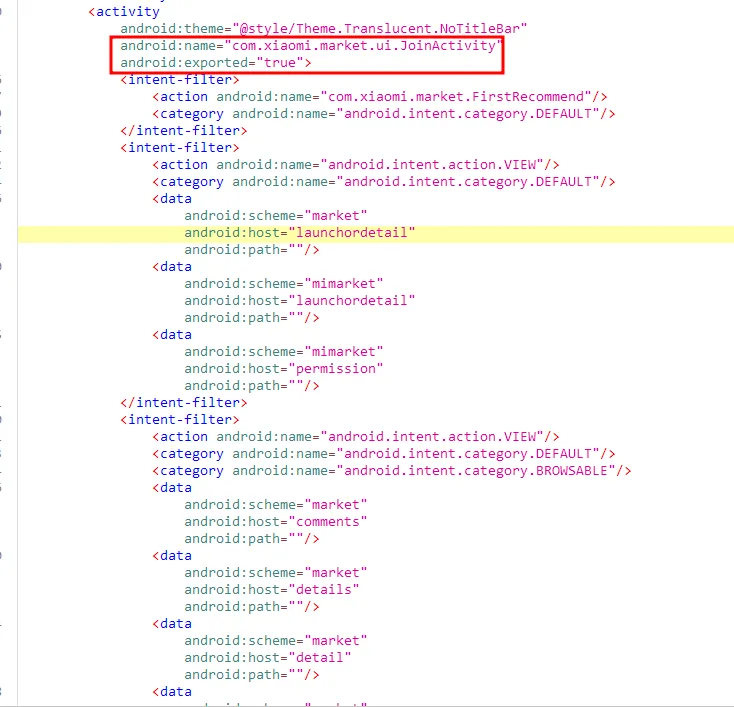
and it exported also use Deaplinks but there to much here but this one used here to exploit this CVE
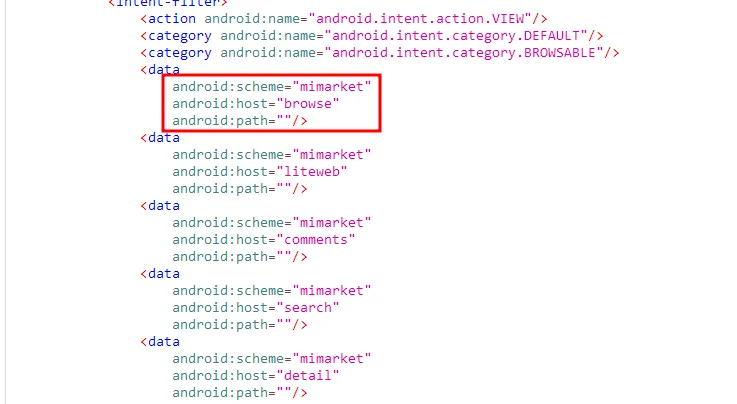
<a id="GetApps" rel="noreferrer" href="intent://browse?url=file%3A%2F%2Fdetail.html#Intent;action=android.intent.action.VIEW;scheme=mimarket;end">Intent</a>
Note: Sometimes app not found this files we are load so just clean storage and reopen it again and try.
Note: this file have 2 version in device first one from assets and another created but as we know from Ken Talk these files are removed Remotely so Xiaomi can Modified this files so first we need to know which folder we are using here so i created file and try to cat it and it worked now i know i’m here in